Overview
A Terraform provider file specifies the configuration needed for Terraform to interact with specific cloud platforms, on-premises systems, or other APIs. Providers serve as plugins that define resources and data sources for particular services. Each provider has its own versioning and settings.
Key Sections of a Provider File
1. Provider Block
The provider block defines the provider and its configurations. For example:
provider "aws" {
region = "us-east-1"
}Explanation:
- The
providerblock specifies which cloud or service provider to use (e.g., AWS, Azure, Google Cloud). - Configuration parameters like
regiondefine the provider’s behaviour. - Dynamic variables (var.region) can be used for flexibility.
2. required_providers Block
This block specifies which providers Terraform should download and use and their sources and versions.
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.0"
}
}
}Explanation:
Source: Specifies the provider’s source. Typically, it is the Terraform Registry (e.g., hashicorp/aws).Version: Specifies the version constraint. Examples include:- >= 4.0: Any version 4.0 or higher.
- ~> 4.0: Any version 4.x but not 5.x.
- = 4.1.0: Only version 4.1.0.
Example 1:
provider.tf:
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.0"
}
}
}
provider "aws" {
region = "us-east-1"
}main.tf
# Create S3 buckets in different regions
resource "aws_s3_bucket" "east_bucket" {
bucket = "my-east-bucket"
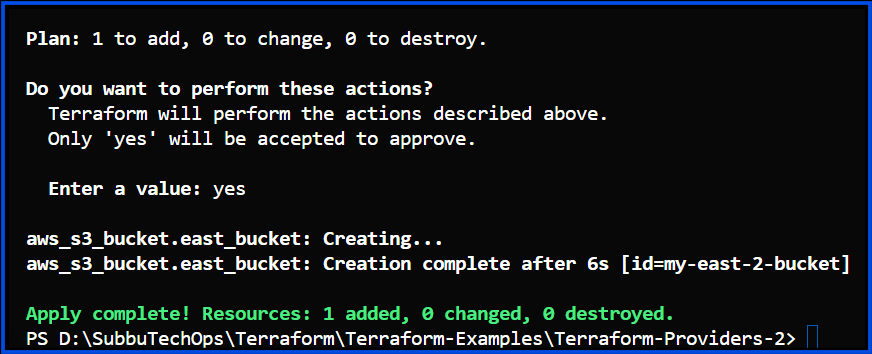
}Output:



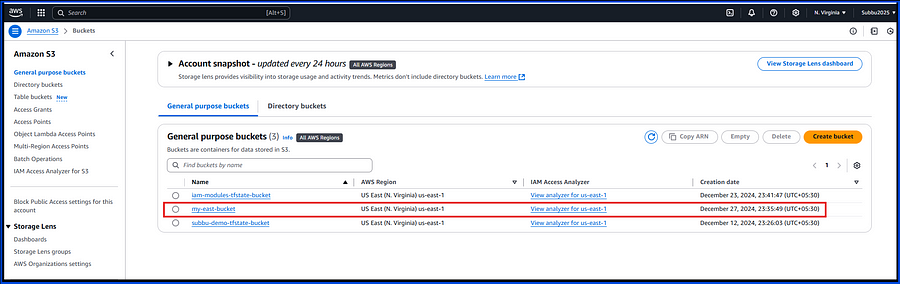
3. required_version Block
This block specifies the Terraform CLI version required to run the configuration.
# Create S3 buckets in different regions
terraform {
required_version = "> 1.5.0"
}Explanation:
- Ensures compatibility between the Terraform CLI and the configuration.
- Examples:
- >= 1.0: Any version 1.0 or higher.
- ~> 1.3: Any version 1.3.x but not 1.4.
- = 1.1.0: Only version 1.1.0.
Example 2:
provider.tf
terraform {
required_version = "> 1.5.0" # allows Terraform CLI version is greater than 1.5.0
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.0"
}
}
}
provider "aws" {
region = "us-east-2"
}main.tf
# Create S3 buckets in different regions
resource "aws_s3_bucket" "east_bucket" {
bucket = "my-east-2-bucket"
}

What Are Provider Aliases in Terraform?
When using the same provider (e.g., AWS or Azure) multiple times in a configuration, you can define aliases to manage resources in:
- Multiple regions.
- Separate accounts or subscriptions.
- Different configurations for staging, production, etc.
Using aliases keeps configurations organized and eliminates duplication.
Explanation:
- Default Provider: The first
awsblock specifies the default configuration for AWS resources. - Aliased Provider: The second
awsblock uses thealiasargument to define an additional provider configuration. - Usage:
- provider = aws: Uses the default provider configuration.
- provider = aws.secondary: Uses the aliased provider configuration.
Use Cases:
- Deploying resources across multiple AWS regions.
- Using different AWS accounts for separate resources.
Example 3: AWS Multi-Region Deployment
Imagine you need to deploy EC2 instances in two AWS regions: us-east-2 and us-west-1.
provider.tf
terraform {
required_version = "> 1.5.0" # allows Terraform CLI version is greater than 1.5.0
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.0"
}
}
}
# Default AWS provider for us-east-1
provider "aws" {
region = "us-east-2"
}
# Aliased AWS provider for us-west-1
provider "aws" {
alias = "west"
region = "us-west-1"
}main.tf
# EC2 instance in us-east-1
resource "aws_instance" "east_instance" {
ami = "ami-036841078a4b68e14"
instance_type = "t2.micro"
provider = aws
}
# EC2 instance in us-west-1
resource "aws_instance" "west_instance" {
ami = "ami-0aa117785d1c1bfe5"
instance_type = "t2.micro"
provider = aws.west
}Output:



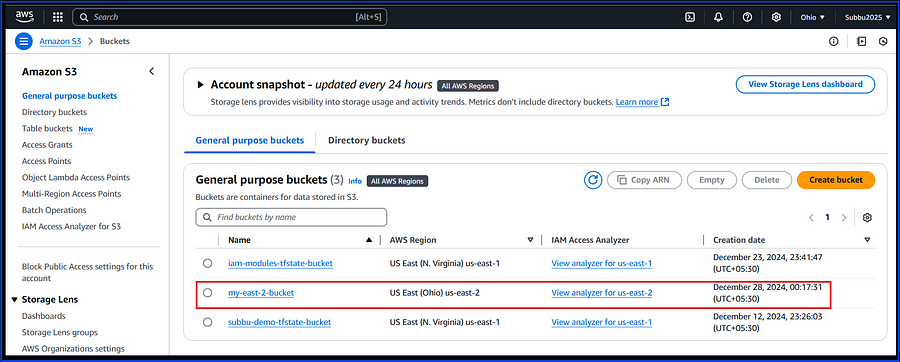
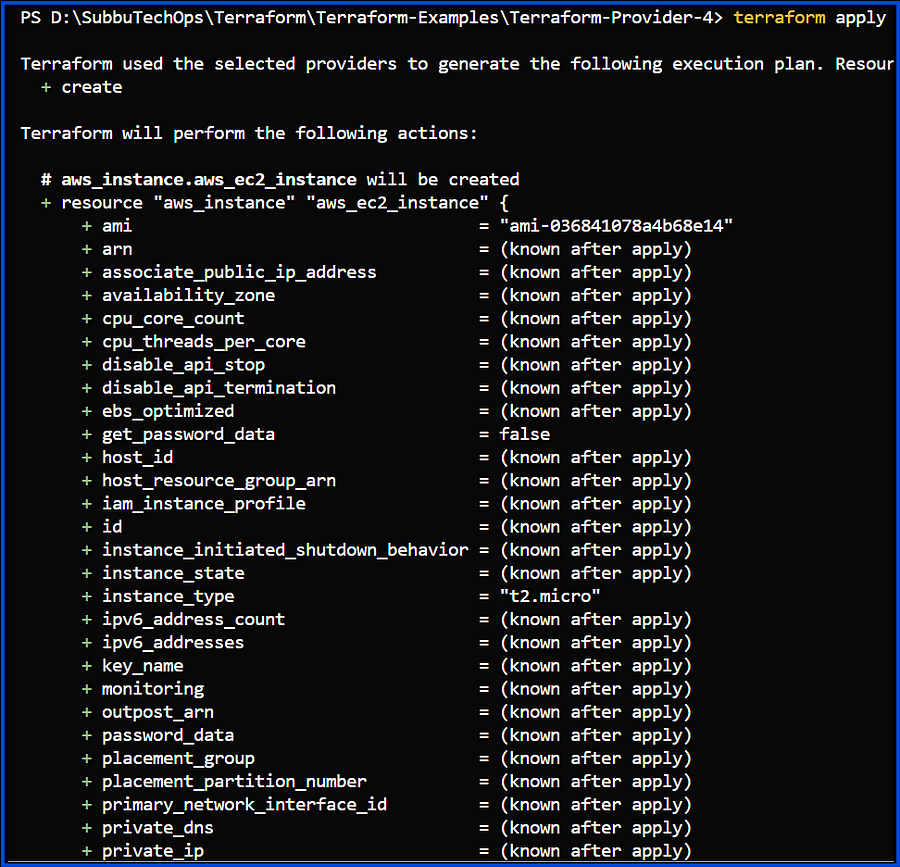
After executing Terraform init, plan, and apply, we can see that both resources are created in their designated regions using the alias concept in the provider block.
Example 4: AWS Multi-Provider Deployment
provider.tf:
terraform {
required_version = "> 1.5.0" # allows Terraform CLI version is greater than 1.5.0
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.0"
}
azurerm = {
source = "hashicorp/azurerm"
version = "~> 3.0"
}
}
}
# Default AWS provider for us-east-1
provider "aws" {
region = "us-east-2"
}
provider "azurerm" {
tenant_id = "c4057555-abc6-4208-bf50-16c68423a0ad"
subscription_id = "99f2c39b-921d-413c-8667-04e952260911"
client_id = "84ddf78a-f5f8-4de6-96de-69f688e36be4"
client_secret = "sGM8Q~N.rnKgGE3AaBJw_k.auDhHSTrlozfNEbn4"
features {}
}main.tf:
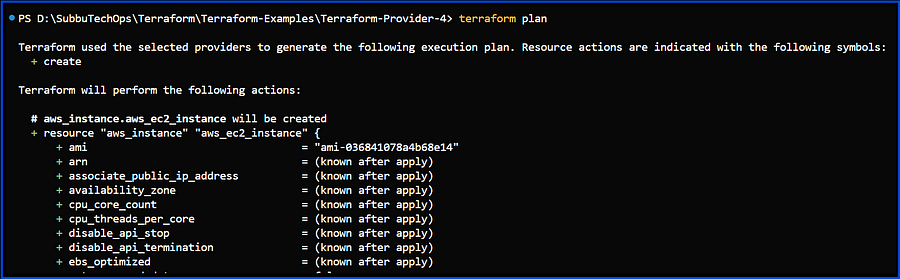
# AWS EC2 Instance
resource "aws_instance" "aws_ec2_instance" {
ami = "ami-036841078a4b68e14" # Replace with a valid AMI for your region
instance_type = "t2.micro"
tags = {
Name = "AWS-EC2-Instance"
}
}
# Azure Resource Group
resource "azurerm_resource_group" "rg" {
name = "terraform-rg"
location = "East US" # Replace with your preferred Azure region
}
# Azure Virtual Network
resource "azurerm_virtual_network" "vnet" {
name = "terraform-vnet"
address_space = ["10.0.0.0/16"]
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
}
# Azure Subnet
resource "azurerm_subnet" "subnet" {
name = "terraform-subnet"
resource_group_name = azurerm_resource_group.rg.name
virtual_network_name = azurerm_virtual_network.vnet.name
address_prefixes = ["10.0.1.0/24"]
}
# Azure Network Interface
resource "azurerm_network_interface" "nic" {
name = "terraform-nic"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
ip_configuration {
name = "internal"
subnet_id = azurerm_subnet.subnet.id
private_ip_address_allocation = "Dynamic"
}
}
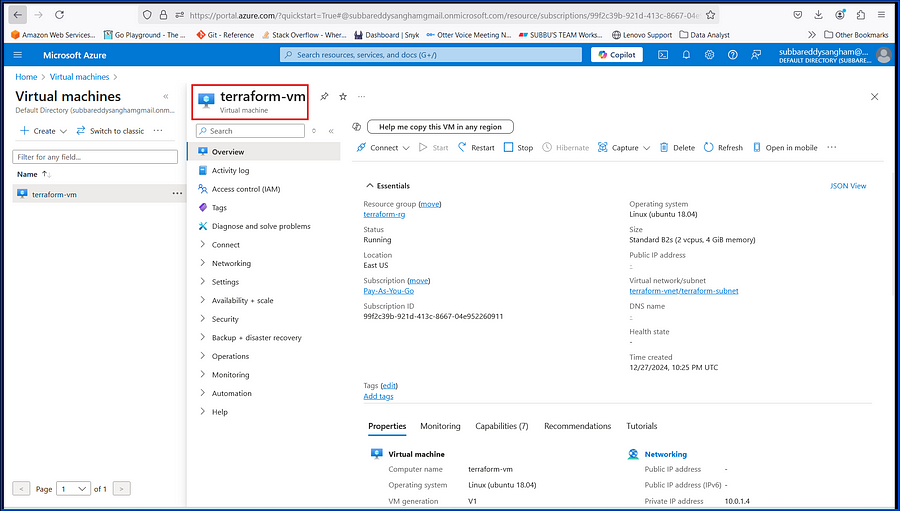
# Azure Virtual Machine
resource "azurerm_linux_virtual_machine" "azure_vm" {
name = "terraform-vm"
resource_group_name = azurerm_resource_group.rg.name
location = azurerm_resource_group.rg.location
size = "Standard_B2s"
admin_username = "azureTestuser" # Replace with a valid username
admin_password = "Password123!" # Replace with a secure password
disable_password_authentication = false # Explicitly allow password authentication
network_interface_ids = [
azurerm_network_interface.nic.id,
]
os_disk {
caching = "ReadWrite"
storage_account_type = "Standard_LRS"
}
source_image_reference {
publisher = "Canonical"
offer = "UbuntuServer"
sku = "18.04-LTS"
version = "latest"
}
}After executing Terraform init, plan, and apply, we can see that both resources are created in their designated regions using the alias concept in the provider block.
Output:


Best Practices for Provider Files:
- Version Pinning:
- Always specify provider versions to avoid unexpected upgrades.
- Use
~>for patch-level compatibility and>=for flexibility.
2. Centralized Configuration:
- Use variables for dynamic configurations like regions, credentials, or profiles.
3. Security:
- Avoid hardcoding sensitive information like access keys. Use environment variables or secret management tools.
4. Lock File:
- Terraform creates a
.terraform.lock.hclfile to ensure consistent provider versions across runs.
Conclusion
The Terraform provider file is a critical part of any Terraform configuration. It defines how Terraform interacts with different services and ensures compatibility through version constraints. By using aliases, you can manage resources across multiple regions or accounts efficiently. Following best practices and using dynamic configurations ensures maintainability and scalability in your Terraform projects.

