Introduction:
Networking forms the backbone of modern IT infrastructure, and it is essential for DevOps professionals to grasp its fundamental concepts. Key topics include IP addressing, CIDR, network models, DNS, load balancing, network security, and network troubleshooting tools. These are crucial for ensuring seamless connectivity and efficient application delivery. In this blog, I will explore the fundamental networking skills that every DevOps engineer needs to effectively manage infrastructure and maintain reliable systems.
This blog is a lengthy read, taking over 20 minutes. It serves as an essential resource. Understanding networking fundamentals is crucial for DevOps engineers.
Computers and computing devices often connect using cables or wireless signals. They use these connections to exchange data. These connections also allow them to share resources, but not all files. This setup is called a network.
A network serves to:
- Facilitate communication between connected devices.
- Users can share resources through a network. They can share music servers, video servers, printers, and scanners.
The Internet is the biggest network in the world. People often call it “the network of networks.”
There are different types of networks. But the main two are LAN and WAN
- LAN (Local Area Network) connects computers within a small area. Examples include homes and schools, like Wi-Fi and Ethernet.
- MAN (Metropolitan Area Network) serves large city areas.
- WAN (Wide Area Network) spreads a LAN across a vast geographic region. Example꞉ optical fiber cable.
- SONET (Synchronous Optical Network) used in submarine, functions under the sea.
Network Components:
1. Switch:
A switch links two or more computers together.
2. Router:
It is a device that is used to connect one network with another.
3. Modem:
A modem helps in the modulation and demodulation processes.
4. Hub:
A hub spreads signals to its connected computers. It acts as a simple power extension device.
5. NIC:
A Network Interface Card (NIC) links a computer to the internet. This card is often wireless and built into the motherboard today. It comes with a Media Access Control (MAC) address.
6. Bridge:
A bridge links multiple local area networks (LANs) to create a larger LAN. It stores the computers’ MAC addresses and cuts down broadcast traffic. The switch has now replaced this device.
What is Protocol?
A network protocol is a set of rules that is set up by people that determine how a particular data is transmitted between different devices in the same network. e.g.: HTTP, TCP, IP, FTP, SMTP, etc.
IP Address and its Types and Classes:
IP Address: An IP (Internet Protocol) address is a unique number assigned to each device on a network, allowing them to communicate with each other. It’s like a device’s “address” on the internet or local network.
Types of IP Addresses
- IPv4:
- 32-bit address, written as four numbers separated by dots (e.g.,
123.89.46.72). - This is a 32-bit IP address, which means it contains a combo of 32 (1 and 0’s). In this version of the IP address, there are 4 groups or Octets (8 bits), and each octet is represented by a decimal value in the address. It is easy to remember.
- Commonly used, but the limited number of addresses (about 4.3 billion).
Example:

2. IPv6:
- 128-bit address, written in eight groups of hexadecimal numbers (e.g.,
2001:0db8:85a3:0000:0000:8a2e:0370:7334). - It provides a vastly larger pool of addresses, designed to replace IPv4 as it runs out.

3. Public IP
– Identifies devices on the internet.
– Internet Service Providers (ISPs) assign these. They are accessible worldwide.
4. Private IP
– Works within private networks like home or office networks.
– Not reachable from the internet. Usually appears as `192.168.x.x`, `10.x.x.x` or `172.16.x.x` — `172.31.x.x`.
5. Static IP
– Assign an address manually. It stays the same.
– Often used for servers and devices needing a steady address. Always the same.
6. Dynamic IP
– A DHCP (Dynamic Host Configuration Protocol) server assigns these automatically.
– Changes over time and often used for devices at home. They vary regularly.
IP Address Classes (IPv4 Only)
The organization [IANA](https꞉//www.iana.org/) (Internet Assigned Numbers Authority) splits IP addresses into various classes. Understanding binary-to-decimal conversion is necessary for this.
IPv4 addresses are separated into five classes. The starting number decides their use in networks.


Note:
- Class A addresses in IPv4 begin from 1.0.0.0 and extend to 126.0.0.0. Address 0.0.0.0 is not included in the Class A range. It serves a special purpose in networking.
- Address 0.0.0.0 has a special role. It is not part of the usable IP addresses in Class A.
127.0.0.0 to 127.255.255.255 represents a special range. This range includes 127.0.0.1 and it is set aside for loopback addresses in IPv4.
What is Loopback?
– A loopback address allows a device to communicate with itself, functioning like a mirror.
– This is commonly used to test network software on the same computer.
Key Points:
- 127.0.0.1 is widely called “localhost.”
– Any IP address within the 127.x.x.x range returns to the same device. It truly circles back.
– Helpful for testing networking applications. External networks are not necessary for this testing.
IP address — Network ID and Host ID
An IP address has two parts꞉ Network ID and Host ID. A Host refers to any device receiving an IP address.
- The Network ID changes with the IP class:
i) Class A꞉ The 1st octet is the Network ID.
ii) Class B꞉ The 1st and 2nd octets form the Network ID.
iii) Class C꞉ The 1st, 2nd, and 3rd octets create the Network ID. - Direct Connection꞉ Devices with identical Network IDs connect without a router.
- Router Need꞉ Devices with different Network IDs require a router.
A simple diagram helps illustrate this topic for clearer understanding.


Subnetting:
Divides a network into smaller and easier parts.
Example꞉ A network with IP address 192.168.1.0/24 becomes subnets like 192.168.1.0/25 and 192.168.1.128/25.
Example of Subnetting
Given network: 192.168.1.0/24
- 192.168.1.0/24 is a Class C network.
- /24 indicates a subnet mask of 255.255.255.0, meaning there are 8 bits for hosts (32 total bits in IPv4–24 bits for the network portion = 8 bits for hosts).
- 192.168.1.0/24 provides 256 IP addresses (from 192.168.1.0 to 192.168.1.255).
Dividing into Smaller Subnets:
To get two equal subnets, use /25 subnet masks. This gives 7 bits for hosts (32–25 = 7 bits for hosts).
- Subnet 1: 192.168.1.0/25
- Range: 192.168.1.0 to 192.168.1.127
- Subnet Mask: 255.255.255.128
- Total IPs: 128 addresses (126 usable for hosts, as the first address is the network address and the last is the broadcast address).
2. Subnet 2: 192.168.1.128/25
- Range: 192.168.1.128 to 192.168.1.255
- Subnet Mask: 255.255.255.128
- Total IPs: 128 addresses (126 usable for hosts).

Explanation
- Using a /25 mask instead of /24 divides the network into two parts. Each part has 128 IP addresses.
- This creates smaller segments within the main network. Managing groups of hosts becomes easier.
Benefits of Subnetting
1. Improves Network Performance꞉ It reduces broadcast domains. Traffic is limited to certain subnets.
2. Strengthens Security꞉ Different departments or functions within a company can be kept separate.
3. Efficient IP Usage꞉ It avoids wasting IP addresses. Only the needed addresses are given to each subnet.
CIDR (Classless Inter-Domain Routing)
CIDR (Classless Inter-Domain Routing) allocates IP addresses and routes IP traffic. This method replaces the old classful network system. CIDR helps use IP addresses more efficiently. It also makes routing simpler.
The table below shows the most common address and netmask combinations. It also provides important details about them.
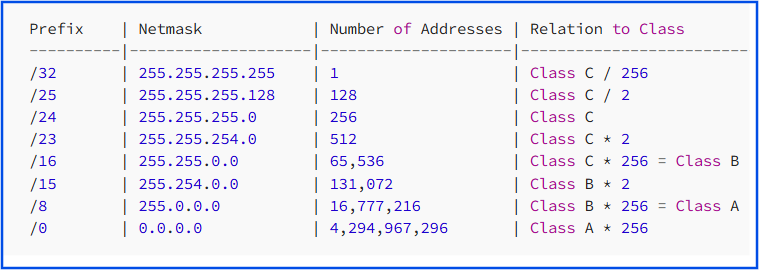
Network Models
There are mainly two types of network model –
- OSI Reference Model
- TCP/IP Model
1. OSI Reference Model
The OSI (Open Systems Interconnection) Model is a set of rules. These rules explain how different computer systems talk over a network. The International Organization for Standardization (ISO) developed the OSI Model. It has 7 layers. Each layer has its own duties and tasks.
- Physical Layer꞉ Manages the physical connection between devices. It sends raw data as bits over cables, radio waves and more.
2. Data Link Layer꞉ Oversees data transfer between devices that are directly connected. Error detection and flow control are its main tasks. Examples are Ethernet and Wi-Fi.
3. Network Layer꞉ Guides how packets move and route through the network. It uses IP addresses. An example is IP (Internet Protocol).
4. Transport Layer꞉ Makes sure data transfers without errors. It controls the flow of data. Examples include TCP and UDP.
5. Session Layer꞉ Builds, keeps and controls communication sessions between apps.
6. Presentation Layer꞉ Changes data formats to make systems compatible. It deals with encryption and compression. An example is SSL/TLS.
7. Application Layer꞉ Directly interacts with the user. It offers network services like HTTP, FTP and SMTP.
Here is a diagram in text form. It shows how the OSI model works from Person X to Person Y.
START: Person X Sends a Message
│
├── Application Layer (Layer 7)
│ └── Prepare message using messaging app protocol (e.g., SMTP, HTTP).
│
├── Presentation Layer (Layer 6)
│ └── Encode/Encrypt the message into a suitable format.
│
├── Session Layer (Layer 5)
│ └── Establish a session with Person Y’s device through the server.
│
├── Transport Layer (Layer 4)
│ └── Break the message into segments and add TCP/UDP headers.
│
├── Network Layer (Layer 3)
│ └── Add source and destination IP addresses for routing.
│
├── Data Link Layer (Layer 2)
│ └── Convert segments to frames and add MAC addresses for delivery.
│
├── Physical Layer (Layer 1)
│ └── Convert frames into bits (0s and 1s) for transmission.
│
└── Transmit through Physical Medium (e.g., Ethernet/Wi-Fi) to Person Y
│
├── Person Y Receives Message
│
├── Physical Layer (Layer 1)
│ └── Receive bits and reassemble into frames.
│
├── Data Link Layer (Layer 2)
│ └── Verify and process frames with MAC addresses.
│
├── Network Layer (Layer 3)
│ └── Extract IP addresses and verify routing information.
│
├── Transport Layer (Layer 4)
│ └── Reassemble segments into data using TCP/UDP.
│
├── Session Layer (Layer 5)
│ └── Verify and maintain the communication session.
│
├── Presentation Layer (Layer 6)
│ └── Decode/Decrypt message into readable format.
│
└── Application Layer (Layer 7)
└── Display the message to Person Y in the messaging app.
END: Person Y Reads the Message
You: (Sender) Friend: (Receiver)
------------------------------------------- -------------------------------------------
Application (HTTP - Port 80) Application (HTTP - Port 80)
↓ ↑
Presentation Presentation
↓ ↑
Session Session
↓ ↑
Transport (Segments - Port 80) Transport (Segments - Port 80)
↓ ↑
Network (Packets) Network (Packets)
↓ (Router Connected: ↑ (Checks Destination IP - 223.7.6.X)
Source IP: 192.75.0.1 Source IP and Destination IP)
Destination IP: 223.7.5.1)
Data Link (Frame) Data Link (Frame)
↓ (Source MAC: 00-0C-29-94-55-05) ↑ (Checks Destination MAC)
(Destination MAC: 00-0E-30-91-51-06)
Physical Layer (Cable - 0100100100) Physical Layer (Cable - 0100100100)
The infographic below explains the seven layers of the OSI reference model.

Below is a list of protocols in each layer of the OSI model with their port numbers:
1. Application Layer (Layer 7):
HTTP (Port 80) ꞉ Web browsing.
HTTPS (Port 443) ꞉ Secure web browsing.
SMTP (Port 25) ꞉ Sending email.
FTP (Ports 20, 21) ꞉ Transfer files.
DNS (Port 53) ꞉ Find domain names.
POP3 (Port 110) ꞉ Email reception.
IMAP (Port 143) ꞉ Get emails.
2. Presentation Layer (Layer 6):
SSL/TLS (Port 443 for HTTPS and others) ꞉ Encrypting data for safety.
MIME꞉ Formats email attachments.
JPEG/PNG꞉ Codes pictures for sharing.
3. Session Layer (Layer 5):
PPTP (Port 1723) ꞉ Creates VPN tunnels.
NetBIOS (Ports 137, 138, 139) ꞉ Starts sessions for talks between networks.
4. Transport Layer (Layer 4):
TCP꞉ Sends data reliably with checks.
UDP꞉ Sends data quickly without checks.
SCTP꞉ Used when many data flows are necessary.
5. Network Layer (Layer 3):
IP (IPv4/IPv6) ꞉ Directs data from start to end.
ICMP꞉ Sends error messages and diagnostics. For example, ping.
IGRP꞉ Shares routing information.
6. Data Link Layer (Layer 2):
Ethernet꞉ Sets physical addresses and channel access.
PPP꞉ Connects points directly.
HDLC꞉ Frames data and controls errors in direct links.
ARP꞉ Matches IP addresses to MAC addresses.
7. Physical Layer (Layer 1):
Ethernet (Physical signaling) ꞉ Details about electrical signals, cables, etc.
USB꞉ Physically attaches devices.
Summary with Ports:
- Application Layer (Layer 7) has well-known protocols with port numbers for communication like (e.g., HTTP — Port 80, HTTPS — Port 443, SMTP — Port 25).
- Layers 2 to 6 handle network management tasks and usually do not use port numbers. These layers control connections and data formats.
Port numbers are important in both the Application and Transport Layers. They help deliver data to the correct programs and services on a computer.
2. TCP/IP Model:
The TCP/IP model or Internet Protocol Suite simplifies the OSI model. It has only 4 layers instead of 7.
This model is practical and works effectively. It contains 4 layers.
- Application Layer = (Application Layer + Presentation Layer + Session Layer) of OSI model
- Transport Layer
- Network Layer
- Network Interface Layer = (Data Link Layer + Physical Layer) of OSI model
(remaining all are same as OSI model discussed above.)
Sender:
Layer 1 → Layer 2 → Layer 3 → Layer 4
↓
(Data is processed layer by layer, encapsulated at each step)
↓
[Network (Router/Internet)]
↓
Receiver:
Layer 4 → Layer 3 → Layer 2 → Layer 1
↓
(Data is processed layer by layer, decapsulated at each step)
The Four Layers of the TCP/IP Model and Their Functions
----------------------------------------------------------
1. Application Layer
-Protocols꞉ SMTP, HTTP/HTTPS, FTP, SSH
Functions:
- The layer creates the data.
- The layer asks for the connection.
2. Transport Layer
-Protocols꞉ UDP, TCP
Functions:
- The layer sets up a data connection without errors.
- The layer divides the data into smaller packets.
- This layer gets a response that packets arrived.
3. Internet Layer
-Protocols꞉ IPv4/IPv6, ICMP, ARP
Functions:
- The layer sends out packets.
- It sends packets correctly.
- This layer directs data to the right network.
4. Network Access Layer
Functions:
- The layer adds the target MAC address.
- It sends data between apps over the network.
- This layer manages the physical setup.
# Ports and Protocols
1. HTTP (Hypertext Transfer Protocol):
It is a client-server protocol. It is stateless, so it never keeps any client data. It explains how a client asks for data from a server. It also explains how the server sends data back to the client.
- When a client asks for data, it is called an HTTP request.
- When a server sends data back, it is an HTTP response. Some HTTP methods ask for data.
GET :- Get some data from server
POST :- Post some form/data to server
PUT :- Put some data
DELETE :- Delete some data in server
Status Codes
Status codes are issued by a server in response to a client’s request made to the server.
There are 4 categories of HTTP responses:
- 200s: Successful responses
- 300s: Redirects
- 400s: Client errors
- 500s: Server errors
Take a look at some of the most common response codes:

Find the full list of status codes with clear explanations by Mr. Abhishek Veeramalla. (Thank you!)
Check here꞉ (https꞉//github.com/iam-veeramalla/http-status-codes/tree/main)
Cookies:
HTTP is a stateless protocol. This means it never stores any client data on the server. Let’s probably get an idea of what cookies are by using an example. Imagine searching for `amazon.com` a second time. Normally, you would be logged out and need to log in again. However, this does not happen. On your second visit, you are already logged in. You see your saved carts and all data. How is this possible? Here, cookies play a role.
Cookies are unique strings stored as files in your browser. When you visit a website for the second time, these cookies send details through HTTP to the server. The server checks them and logs you in automatically.
2. SMTP/POP (Simple Mail Transfer Protocol and Post Office Protocol):
- SMTP helps send and receive emails. Emails go from the sender’s SMTP server to the receiver’s SMTP server.
- POP downloads emails from the POP server.
3. FTP (File Transfer Protocol):
- FTP helps people download, upload and move files between different computers. Files travel easily using FTP.
4. Secure shell (SSH):
- Similar to Telnet. System administrators use it to connect safely to a computer over an unsafe network. This connection is secure.
5. TCP (Transmission Control Protocol):
- Reliable and connection-oriented protocol.
- Sends data accurately with acknowledgements and retransmissions if necessary.
- Suitable for applications where data accuracy is crucial.
- Example: HTTP (port 80), SQL (port 1433).
TCP and the Three-Way Handshake:
Before transmitting packets, TCP must ensure that a stable connection has been set up between the sender and the recipient. This is where the three-way handshake (or SYN-SYN-ACK) comes in.
The three-way handshake, known as SYN-SYN-ACK, helps set up this connection.

2. UDP (User Datagram Protocol)
- An unreliable and connection less protocol.
- Provides no acknowledgements and no retransmissions. Delivers data faster but without delivery guarantee.
- Serves applications valuing speed over reliability.
- Example applications include video streaming and DNS queries.
Find the link below for Common Ports and Protocols Cheat Sheet (Thanks to Stationx):
Common Ports Cheat Sheet: The Ultimate List
Routing
How do we send a packet of information from a host on one network to a host in another?
Routing solves this problem.
The Importance of Routing:
Routing is crucial for linking networks and allowing smooth data transfer. Routers use routing tables and protocols. These tools help them decide intelligently how to forward packets. This process allows communication between devices on different networks.
Routing Tables:
- A routing table is like a GPS for routers. It contains:
- Network Destination: The IP address of the target network.
- Subnet Mask: Specifies the range of IP addresses in a network.
- Gateway: The next-hop router IP address.
- Interface: The router interface that forwards the packet.
Example of a routing table:
Destination Subnet Mask Gateway Interface
192.168.1.0 255.255.255.0 192.168.1.1 eth0
10.0.0.0 255.0.0.0 10.0.0.1 eth1
Default Route 0.0.0.0 192.168.1.254 eth0
The Routing Process
- Packet Sent:
- A packet starts its journey from a source host. It includes the destination IP address in its header.
2. Router Receives the Packet:
- The router checks its routing table to find the best route for the packet.
3. Packet Forwarded:
- The router sends the packet to the next hop based on the routing table.
4. Repeat Until Destination:
- This activity goes on until the packet arrives at the destination host. It travels step by step.
We use routing tables to decide which routes to follow. This screenshot shows a typical route table in AWS.

When making a routing decision, more narrow rules are evaluated first:
- If a packet destination is in a range of 10.21.0.0/16 — it will remain in a local network (your neighborhood).
- If a packet destination is in a range of 10.0.0.0/8 — it will be sent to the transit gateway (TGW) interface (your state highways).
- If a packet destination does not fall in any of these ranges, the widest one is evaluated which is 0.0.0.0/0 which means it is internet traffic. And the packet will be redirected to the Network Address Translation (NAT) interface.
DNS (Domain Name System)
DNS (Domain Name System) translates human-readable domain names (e.g., www.example.com) into IP addresses (for example, 192.0.2.44).
Root DNS Server stores all the Top-level domain e.g : — .com, .in, .org, .io etc.
DNS works like the phone book of the internet, allowing humans to use readable names while machines use numerical addresses.
How DNS Works
- You type a website address (e.g., `www.example.com`) into your browser. The browser needs the IP address of that server.
- The DNS process involves finding the domain name. It looks for the matching IP address through multiple DNS servers.
Example: Visiting a Website “www.example.com”
Step 1: User Request
- Action: You type "www.example.com" in your browser.
Step 2: DNS Query
- Action: The browser sends a request to the DNS server for the IP address
of "www.example.com".
Step 3: DNS Resolution
- The DNS server:
- Checks its cache for the IP address.
- If not found:
- Contacts Root DNS Server → TLD DNS Server → Authoritative DNS Server.
Step 4: IP Address Found
- Result: The DNS server resolves the domain to an IP address
(e.g., 93.184.216.34).
- Sends the IP address back to your browser.
Step 5: Connecting to the Website
- Browser uses the IP address to establish a connection with the web server.
- Result: The website content loads on your screen.
Domains, Zones, and Delegation:
- Domains: Domains are like branches in a tree-like structure of the internet. The root domain sits at the highest level. Next come top-level domains (TLDs) like `.com` or `.org`. Subdomains, such as `example.com`, extend from TLDs.
- Zones: A zone is a portion of the domain that is managed by a specific organization. For instance,
.comis a zone controlled by Verisign. ICANN manages the root zone at the top of the DNS tree, while different organizations manage subdomains. - Delegation: Delegation lets an organization transfer control over part of a domain to another group. This transfer uses Nameserver (NS) records.
- For example, ICANN controls the root domain and delegates
.comto Verisign. - Verisign might then pass control of `example.com` to “Example Ltd.” They would do this by adding an NS record pointing to the nameserver of “Example Ltd.”
NS records send internet traffic to the right nameserver. This nameserver controls a domain. Different parts of the DNS tree are managed separately. Different organizations handle these parts independently.

DNS record types:
DNS records, also known as zone files, provide information about a domain. They include the IP address for the domain and instructions for managing inquiries. Each DNS record contains a time-to-live setting (TTL). This setting shows how often a DNS server refreshes the record.
Below are the most commonly used types of DNS records and their meaning:
Type Name Description
--------------------------------------------------------------
A Host Address Maps domain names to IPv4 addresses.
AAAA IPv6 Host Address Maps domain names to IPv6 addresses.
CNAME Canonical Name Maps a name to another name (alias).
No other records allowed.
ALIAS Auto Resolved Alias Maps a name to another name; can coexist with other records.
MX Mail Exchange Specifies email servers for a domain.
NS Name Server Points to DNS servers responsible for a domain.
TXT Descriptive Text Holds domain-related info; often used for verification.
DHCP
DHCP (Dynamic Host Configuration Protocol) is a network management protocol that automatically assigns IP addresses and other network configurations (such as subnet mask, gateway, DNS servers) to devices on a network.
Example:
- When you connect your laptop to a Wi-Fi network, a DHCP server assigns it an IP address automatically, allowing it to communicate with other devices on the network without manual configuration.
Network Components and Services
Firewalls
Firewalls control incoming and outgoing network traffic based on predetermined security rules.
Load Balancers
Load balancers distribute incoming network traffic across multiple servers to ensure no single server becomes overwhelmed.
VPN
VPN (Virtual Private Network) provides a secure connection between remote users and the corporate network over the internet.
Network Troubleshooting Tools:
1. ping
- Purpose: Test internet network connections.
- How It Works: Uses the ICMP ECHO_REQUEST to get an ICMP ECHO_RESPONSE from a remote host.
- Usage: For basic troubleshooting, for example you can run
ping www.google.comto check network connectivity and see response times and packet loss.

2. traceroute (or tracert on Windows)
- Purpose: Track the route packets take to reach their destination.
- How It Works: Sends UDP probes with increasing TTL values, showing each router along the route and the delay in reaching it.
- Usage: Helps find which gateway is causing a delay by showing response times and where packets fail (indicated by “).
Common Use Cases:
- Diagnosing Network Latency: Locate where delays occur in the network.
- Identifying Routing Problems: Detect loops or unintended routes.
- Checking Connectivity Issues: Determine if the destination is reachable.
- Monitoring ISP Performance: Check if an ISP’s routing is optimal.

3. telnet
- Purpose: Test network connections and protocols.
- How It Works: Attempts to establish a connection to a specified IP and port.
- Usage: Test if a specific service is reachable, e.g.,
telnet www.google.com 80.

4. curl
- Purpose: Transfer data using multiple protocols, often for HTTP requests.
Key Features of curl:
- Protocol Support: Handles HTTP, HTTPS, FTP, SCP, SFTP, LDAP, and more.
- Customizable Requests: Send GET, POST, PUT, DELETE, or other HTTP methods.
- Header Manipulation: Add or modify headers in the request.
- Data Transfer: Upload or download files directly.
- Authentication: Supports basic, token, and other authentication methods.
- Debugging Tool: Provides detailed output for troubleshooting.
Usage:
- Basic GET request:
curl <http://example.com>. - Check headers:
curl -I <http://example.com>. - POST request:
curl -X POST <http://example.com>. - Save response to file:
curl <http://example.com/file> -o output.file.

5. dig (Domain Information Groper)
- Purpose: Troubleshoot DNS problems and verify DNS records.
- How It Works: Performs DNS lookups and displays information such as IP addresses.
Key Features of dig:
- Query DNS Records: Fetches records like A, AAAA, MX, TXT, CNAME, and more.
- Custom DNS Servers: Allows queries against specific DNS servers.
- Debugging DNS Issues: Diagnoses problems like incorrect DNS records or propagation delays.
- Detailed Output: Offers comprehensive data, including response times and record details.
- Usage:
dig google.comto get information like IP addresses, TTL, and DNS record types.

6. netstat
- Purpose: Show network connections and port listening information.
Usage:
netstat -lp: List listening servers and their program names.netstat -a: Show all active ports.netstat -r: Show routing table.
Common Use Cases of netstat:
i) Monitor Open Ports and Connections:
- See active TCP/UDP connections and listening ports.
ii) Check Process and Port Mapping:
- Identify which application is using a specific port.
iii) View Routing Table:
- Analyze the kernel’s routing table to understand network traffic paths.
iv) Diagnose Network Issues:
- Troubleshoot connectivity, packet drops, or network congestion.
v) Monitor Network Interface Statistics:
- Check packet transmission/reception stats.
Ex: netstat -tulnp
The command netstat -tulnp shows a detailed list of network sockets that are listening. It also shows the processes connected to them.

Note:
The ss (socket statistics) command is probably the primary choice in modern Linux distributions. This happened because it works faster and offers more features compared to netstat.

7. nmap (Network Mapper)
- Purpose: Discover hosts and services on a network.
- How It Works: Sends raw packets to identify hosts, services, and operating systems.
Usage:
- Discover hosts:
nmap -sn 172.31.44.35/20. - Scan ports on a host:
nmap -A 172.31.36.237.

For example, we try to examine the network of a Docker container by using the nmap command.
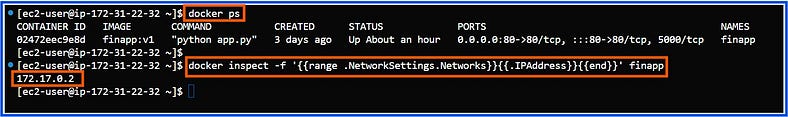

8. ssh (Secure Socket Shell)
- Purpose: Securely connect to remote machines to execute commands.
Usage:
- Connect to a server:
ssh username@hostname. - Secure and encrypted, used for remote management and file transfers.
9. scp (Secure Copy Protocol)
- Purpose: Securely copy files between local and remote hosts.
Usage:
- Copy file to a remote server:
scp localfile.txt user@remote:/path/to/destination.
For example to transfer my SSH key (linuxkey.pem) from my local machine (Windows) to my EC2 instance (/home/ec2-user/ directory) using scp, follow these steps:
Command to Transfer File:
Run this command on your local Windows machine:
scp -i "C:\Users\ssrmc\Downloads\linuxkey.pem" "C:\Users\ssrmc\Downloads\linuxkey.pem"
ec2-user@<EC2-PUBLIC-IP>:/home/ec2-user/

Once the above command is executed, it validates the connection with the EC2 instance using its IP address. If the authentication is successful, the specified file is securely copied to the designated directory on the EC2 instance.

These tools are invaluable for network diagnostics, troubleshooting, and secure communications, which are critical skills for any DevOps engineer.
Conclusion:
In the real world, picture setting up a cloud-based shopping app using micro services. Networking plays a very important role at each step. IP addresses give each container a special ID for smooth communication. DNS converts user-friendly links like shop.example.com into server IPs. Load balancers spread incoming traffic evenly across many servers. This helps during busy times like sales.
Meanwhile, network security uses things like firewalls and VPNs to guard customer data. Network tools watch for problems like slow speeds or lost connections. Solving these issues quickly is essential. Knowing these important networking ideas really helps. You build strong, secure and expandable systems that fit actual needs.
Join me on this journey of learning and sharing as we explore the world of networking, DevOps, and IT practices together. Your feedback and suggestions are invaluable in helping us grow and improve. Let’s make this journey insightful and impactful—together!

